Apple, Google, Facebook hit by 16 billion registration data violations: crypto users on maximum alert
In what cybersecurity experts are calling one of the most severe data infractions in modern history, more than 16 billion records, including user names, passwords, tokens and metadata, linked to important technological platforms such as Apple, Google, Facebook, Github and Telegram have been exposed online. This unprecedented escape, first discovered by Cybernews researchers, is raising serious concerns not only for common users but also for those in the cryptocurrency sector, where bets are especially high.
What we know about violation
According to Cybernews, the violation was the result of a massive collection of compromised data that cover 30 different sets of data, many of which contained millions or even billions of login credentials. These data sets were discovered insectively in cloud servers and elasticsearch databases, which makes them easily accessible to cybercriminals.
What distinguishes this violation is its scale and freshness. Unlike some leaks that circulate for years before coming to light, many of the records in this violation seem to be recent, collected through sofisticated malware known as “infent of infants.” These malicious software programs infiltrate devices, diverting confidential data, such as email addresses, passwords, authentication tokens, cookies and device metadata without user knowledge.
Cybernews reports that these data could allow attackers to orchestrate phishing schemes, make accounts and launch scams almost immediately. The speed at which these credentials can be exploited leaves a little time for users to react once their accounts have compromised.
Why the cryptographic community should be alarmed
While this violation has clear risks for all Internet users, cryptocurrency holders face a particular danger. Many exchanges of encryption and wallet services continue to depend on the basic session logs and raisins for access to the account. If the attackers enter these accounts using stolen credentials, they can empty wallets in minutes.
Risks are not limited to individual investors. Cryptocurrency exchanges and decentralized finance platforms (DEFI) are potential objectives. Without rigorous security protocols instead, these platforms could suffer violations that compromise not only user funds but also in the broader cryptographic ecosystem. Experts warn that, as in the coinbase and high profile binance tricks of the past, the vulnerabilities exposed by filtered credentials could lead to catastrophic financial losses.
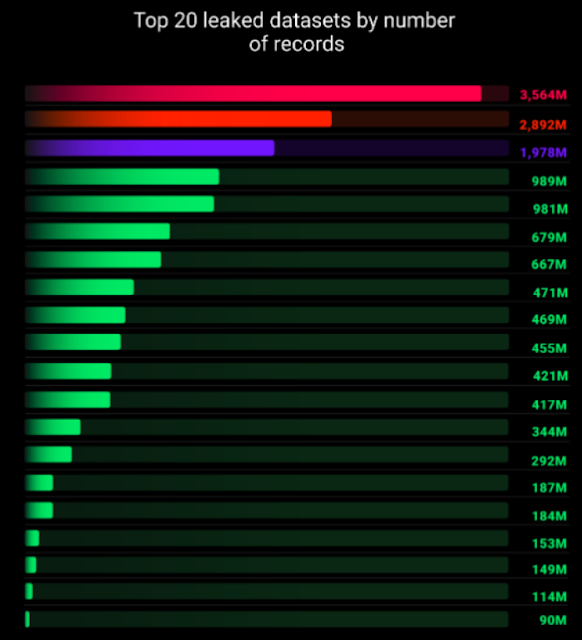 |
| Source: Cybernews |
Custody wallets, those administered by exchanges in the name of users, are especially vulnerable. If a hacker wins email control linked to said wallet, you may be able to restore passwords, alter security configuration and take advantage of total fund control.
The Nobitex Hack: A recent case study
The severity of this violation becomes even clearer in the light of recent events. Earlier this year, the largest cryptocurrency exchange in Iran, Nobitex, suffered a devastating hack in which more than $ 90 million were stolen in cryptographic assets. While research is ongoing, cybersecurity analysts believe that stolen credentials played a role in facilitating that attack.
With the addition of 16 billion new records that now circulate on the dark website, experts fear that we can see similar or even larger -scale attacks on the near future. Cryptographic investors and platforms are urged to act decisively to strengthen their defenses.
What immediate steps should encryption users take?
The large size and recipio of this data violation should serve as a call to urgent action. If it is a cryptocurrency user, or even if you simply have confidential accounts online, now it is time to review your safety practices. Experts recommend taking the following steps without delay:
-
Change your passwords: If you use the same password in multiple sites, or if your passwords have not been updated in a time, change them now. Make sure each password is strong and unique.
-
Enable two factors authentication (2FA): Whenever possible, activate 2FA. This adds a second critical protection layer that can avoid unauthorized access even if your password is compromised.
-
Ensure your private keys: Never store wallet seed phrases, recovery words or private keys in cloud services or devices that may be vulnerable to attack. Use out -line storage solutions instead.
-
Stay attentive to phishing: Be careful with emails, messages or calls not requested that request confidential information. Atcakes often use violated data to create convincing phishing attempts.
-
Monitor your accounts: Be attentive to the activity of your cryptographic wallet and account login. Unusual or unauthorized activity should be informed and act immediately.
A call for industry
It is likely that the consequences of this violation resonate in the sectors of technology and finance. For the cryptocurrency industry in particular, it highlights an urgent need for stronger safety standards. Exchanges, wallet suppliers and Defi platforms should do more to protect their users, from the implementation of stricter authentication measures to educate customers about best practices.
In addition, regulators and policy formulators can use this event as an additional justification to adjust cybersecurity requirements for cryptographic companies. As the mature digital asset space, robust security will be a key factor in determining which platforms win and retain user confidence.
Final thoughts
The exhibition of 16 billion records linked to some of the world’s largest technological giants is more than another holder: it is a marked reminder of the vulnerabilities that exist in our increasingly digital lives. For cryptocurrency users, risks are magnified by the irreversible nature of blockchain transactions. Once funds are stolen, they are almost impossible to recover.
This violation should not be seen as a reason to abandon cryptography or digital innovation, but rather as a call to action for people and organizations to seriously take cyber security. The tools to protect us exist, but it depends on us to use them before it is too late.
Writer
@Erlin
Erlin is an experienced cryptographic writer who loves to explore the intersection of blockchain technology and financial markets. She regularly provides information about the latest trends and innovations in the currency space.
See other news and articles on Google News
Discharge of responsibility:
The articles published in Hokanews are intended to provide updated information on various topics, including cryptocurrency and technology news. The content on our site is not intended to be an invitation to buy, sell or invest in any asset. We encourage readers to conduct their own research and evaluation before making an investment or financial decision.
Hokanews is not responsible for any loss or damage that may arise from the use of the information provided on this site. Investment decisions must be based on an exhaustive investigation and advice of qualified financial advisors. Information about Hokanews can change without prior notice, and we do not guarantee the precision or integrity of the published content.


