Bigone Exchange hit by hack of the supply chain of $ 27 million: What did badly, what follows?
In what is emerging as one of the most related incidents of the year, Bigone ExchangeAn outstanding global cryptocurrency trade platform has confirmed that it has suffered a Safety breach of $ 27 million. Unlike many hacks that exploit the vulnerabilities of the wallet, this attack took advantage of a rare but increasingly worrying method: a Back -End supply chain exploitation that the user wallets completely obvious.
An unconventional attack that saute the wallets
He Bigone Exchange Attack It did not imply stolen private keys or compromised hot wallets, cryptography robbery compalle of the robberies. On the other hand, according to a detailed report by the security company HandkerchiefThe attackers infiltrated Bigone Production Networkmanipulating how servers processed accounts and verifications of internal risks.

This manipulation allowed them to avoid traditional and silent security triggers Transfer funds without immediate detectionExpose a chilling reality for encryption exchanges: even if the user’s wallets are blocked, vulnerabilities within backend systems can lead to substantial losses.
How the hackers violated the production network
The attackers attacked Bigone live production environmentThe operational spine of the exchange that handles millions in the volume of daily trade. Instead of suspending commercial or blocking systems, computer pirates altered how retirement requests in the backend were verified. This allowed them to simulate legitimate transactions, systematically diverting funds into multiple blockchains.
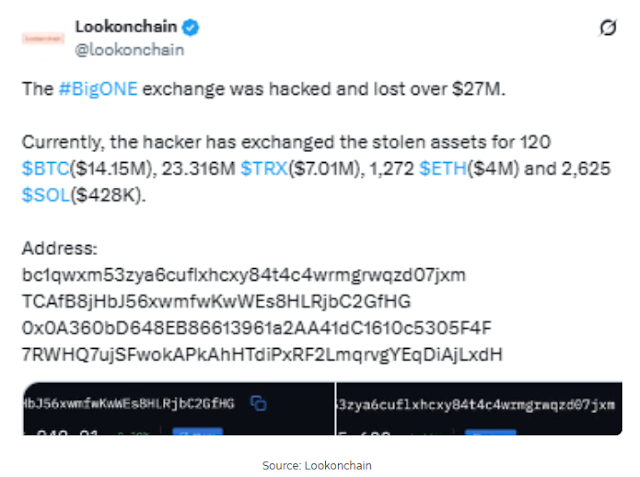
The scope of theft: assets, quantities and addresses
Blockchain Lookonchain analysis platform He tracked the funds, revealing that the attackers successfully withdrew more than $ 27 million in Bitcoin (BTC), Ethereum (ETH), Tether (USDT), Solana (Sun) and Xinfin (Xin).
The stolen assets moved quickly to several directions and became:
Traced addresses linked to attackers include:
-
bc1qwxm53zya6cuflxhcxy84t4c4wrmgrwqzd07jxm -
TCAfB8jHbJ56xwmfwKwWEs8HLRjbC2GfHG -
0x0A360bD648EB86613961a2AA41dC1610c5305F4F -
7RWHQ7ujSFwokAPkAhHTdiPxRF2LmqrvgYEqDiAjLxdH
These rapid transactions suggest a well coordinated operation Designed to quickly obscure the path and fund washing before the monitoring companies of the application of the law or blockchain monitoring can intervene.
Bigone’s official response and immediate action
After the discovery of rape, Bigone Exchange immediately suspended withdrawals contain the damage and avoid more unauthorized transactions. Trade and deposits will be resumed shortly, but the withdrawals will remain detained to a Integral Security Audit and Backend Review They are completed.

In a statement to users, Bigone emphasized that User wallets or private keys were not committed. The violation was completely within its backend operating systems, ensuring that user funds remain safe from direct wallet theft, but the event has generated concerns about hidden systemic vulnerabilities.
Complete compensation and promised transparency
To restore user confidence, Bigone announced that Cover the stolen funds of your reservations completelyensuring that no user supports the financial loss of violation. The exchange has committed to regular updates Throughout its system’s research and restoration process, promising transparency during this critical period.
An increasing trend: Backend exploits in crypto
This incident follows a worrying trend in the cryptocurrency industry. In recent weeks:
-
GMX lost more than $ 42 million in a suspicion of exploit.
-
NobitexThe biggest exchange of Iran, suffered a $ 90 million rape.
These incidents collectively underline the Tactics in evolution of cybercriminals Those who are moving away from traditional wallet exploits for backend infrastructure attacks, often taking advantage of past vulnerabilities overlooked or without blinking in systems that support cryptographic trade operations.
Why Back -End vulnerabilities represent a severe risk
Unlike wallet hacks, backend rapes can even ignore even the safer wallet infrastructure when addressing the environment where wallet interactions are authorized. In the case of Bigone, the attackers manipulated the logic of transaction verification, a critical security layer aimed at safeguarding against unauthorized retreats.
If Backend’s vulnerabilities remain without control, even exchanges with robust wallet management systems could be exposed, doing Backend hardening as crucial as wallet safety.
Implications throughout the industry and the need for surveillance of the supply chain
He Bigone Exchange Attack is a attention call for cryptographic industry. As the exchanges scale often integrates multiple third -party services for KYC, liquidity management, analysis and housing in the cloud, introducing the complexity of the supply chain.
Each third party dependence becomes a potential vector for the attack. If these are even compromised, indirectly, attackers can obtain support points within operational infrastructure, avoiding front-end security layers. This requires:
-
Integral Security Audits of third -party integrations.
-
Implementation of zero trust architecture within operational workflows.
-
Real time monitoring for abnormal backend activities.
User trust and market stability
Immediately after the attack, concerns about user safety and market stability extend throughout the cryptographic ecosystem. However, Bigone’s commitment to total compensation and transparent investigation has helped mitigate user panicavoiding a massive user exodus and stabilizing commercial feeling.
For cryptographic investors and merchants, the incident underlines the importance of evaluating the operational security of an exchange, not only its frontal policies or wallet management capabilities.
The way to recovery and future measures
The Bigone Roadmap for recovery includes:
-
A exhaustive forensic investigation in the exact mechanisms of the attack.
-
Backend infrastructure update To patch vulnerabilities.
-
Implementation of advanced monitoring systems To detect unusual transaction patterns.
-
Regular penetration test and supply chain evaluations.
Trade and deposits are expected to return in phases, while retreats will only be reopened after a rigorous validation of the system.
Final thoughts: a lesson for all exchanges
The Bigone Exchange attack highlights a critical aspect but often overlooked the safety of cryptography: The vulnerabilities of the backend chain and supply are as dangerous as the wallet exploits. Exchanges must adopt a holistic safety approach, protecting each layer from the Fronte user interface to the logic of backend and third -party integrations.
For users, this is a reminder to diversify assets on multiple platforms, use cold storage when possible and stay informed about the security practices of exchanges in which they trust their funds.
As the cryptographic industry grows and matures, only the platforms that proactively address these evolutionary threats will retain user confidence and lead in a competitive panorama.
Writer
@Ellena
Ellena is an experienced cryptographic writer who loves to explore the intersection of blockchain technology and financial markets. She regularly provides information about the latest trends and innovations in the currency space.
See other news and articles on Google News
Discharge of responsibility:
The articles published in Hokanews are intended to provide updated information on various topics, including cryptocurrency and technology news. The content on our site is not intended to be an invitation to buy, sell or invest in any asset. We encourage readers to conduct their own research and evaluation before making an investment or financial decision.
Hokanews is not responsible for any loss or damage that may arise from the use of the information provided on this site. Investment decisions must be based on an exhaustive investigation and advice of qualified financial advisors. Information about Hokanews can change without prior notice, and we do not guarantee the precision or integrity of the published content.


